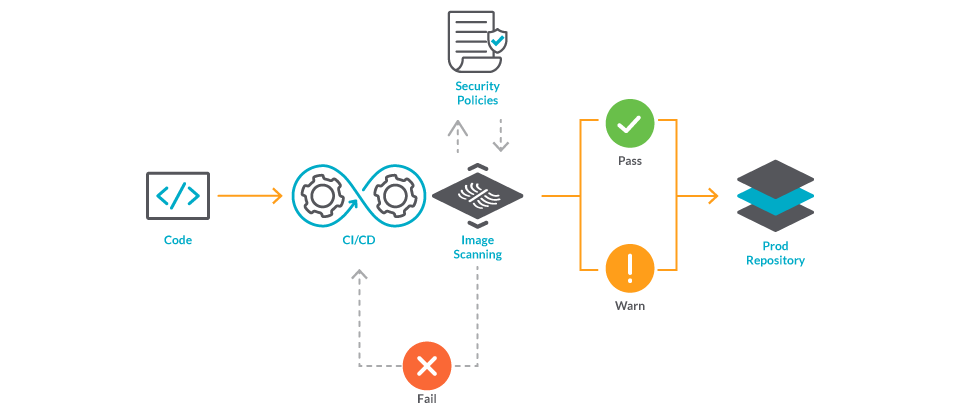
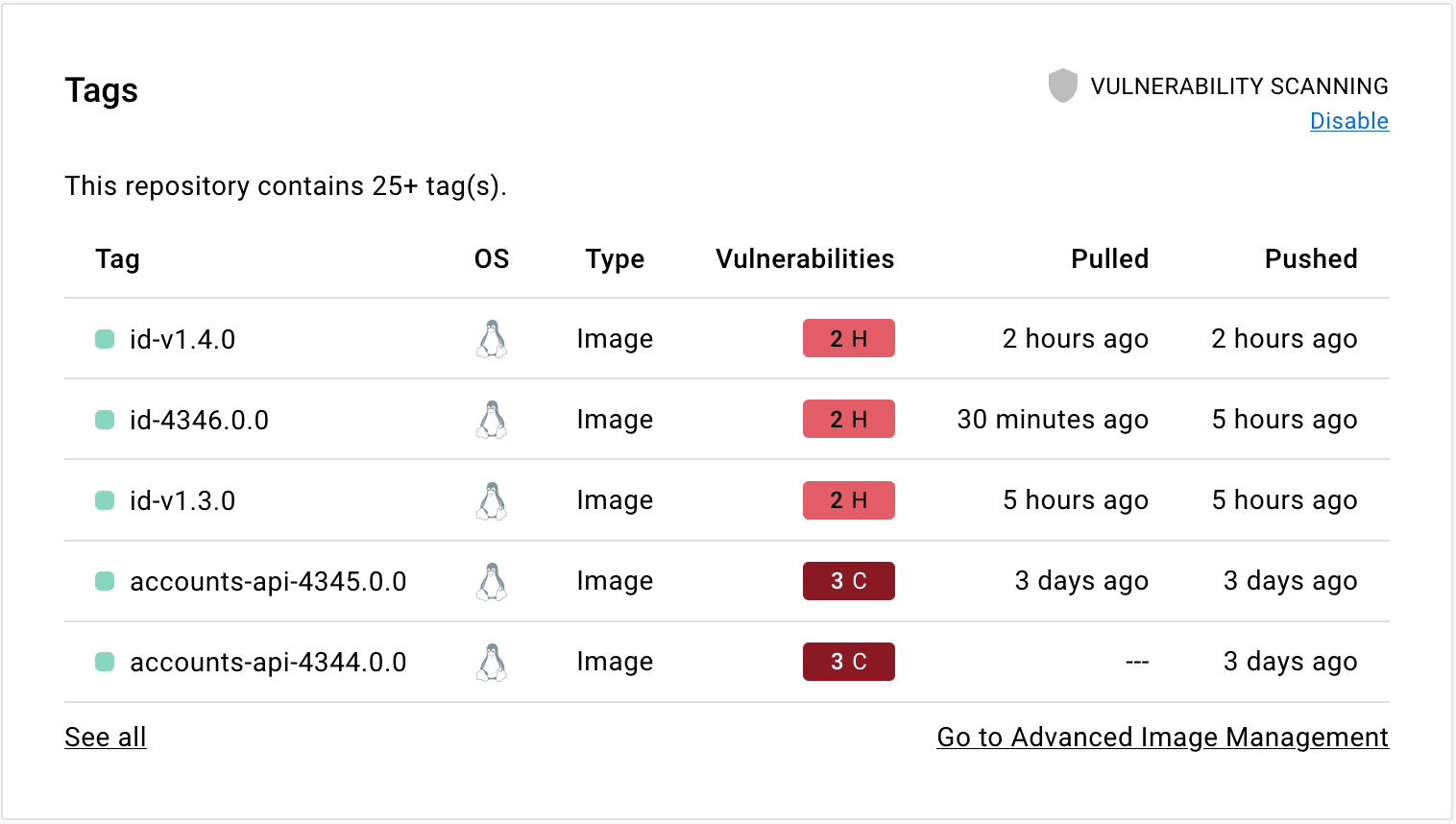
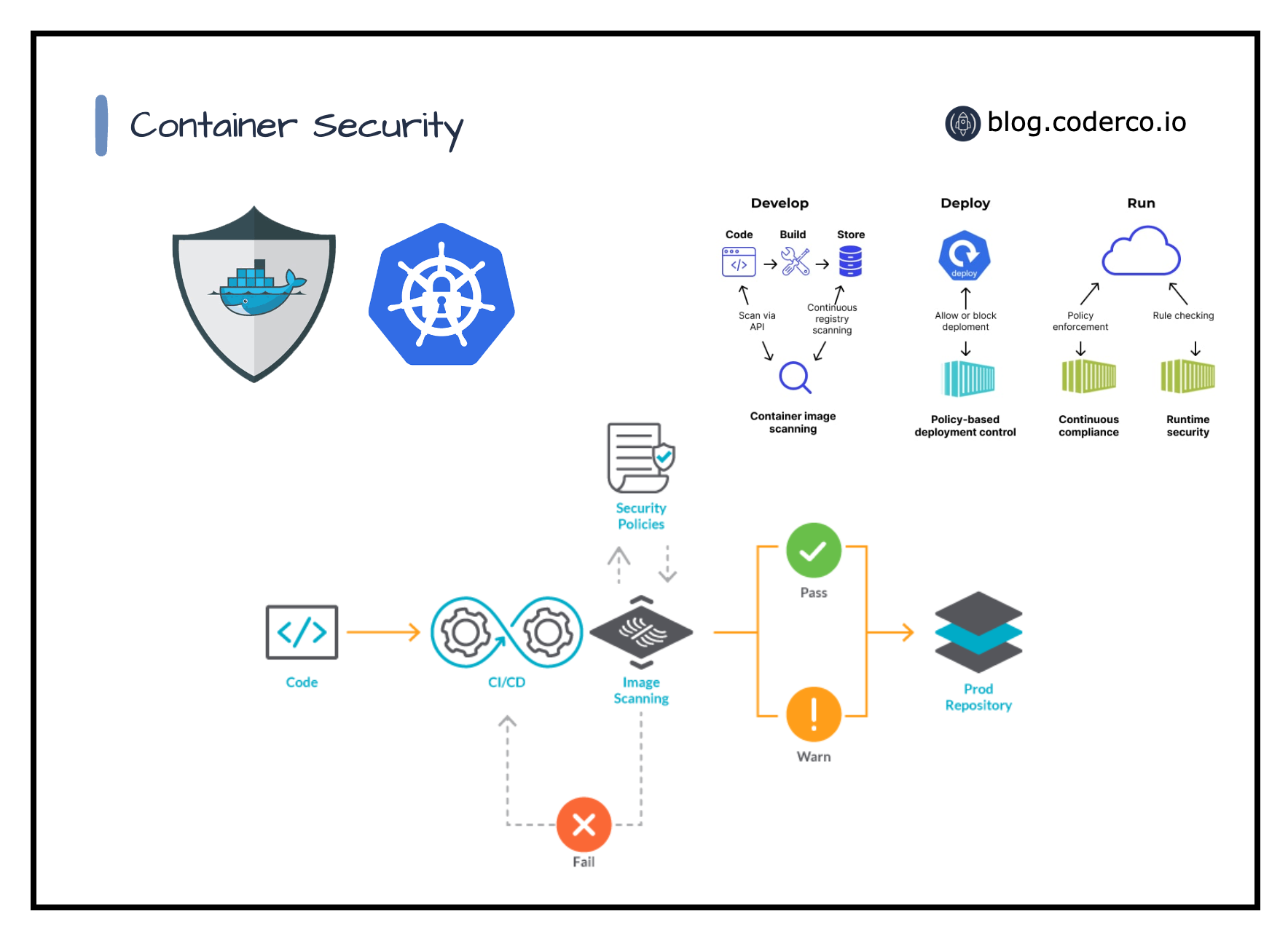
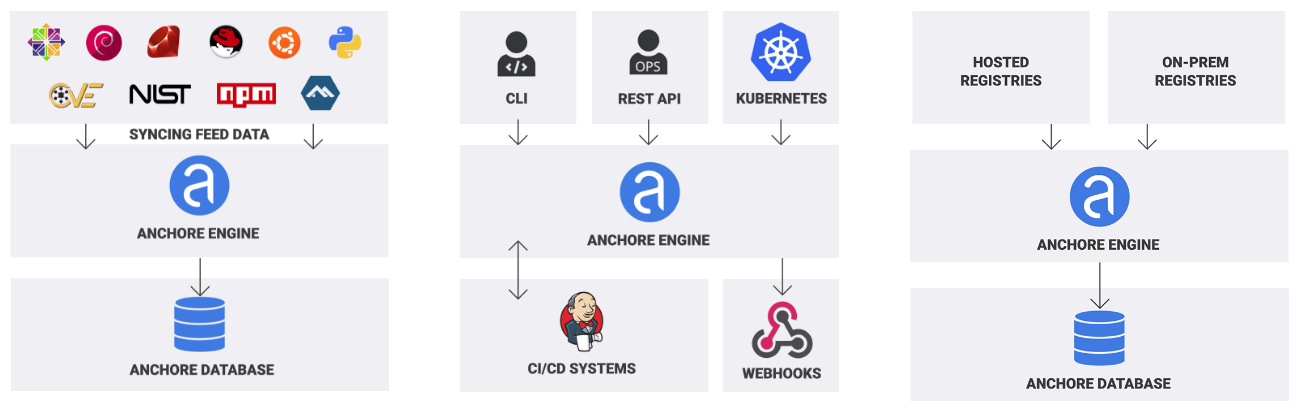
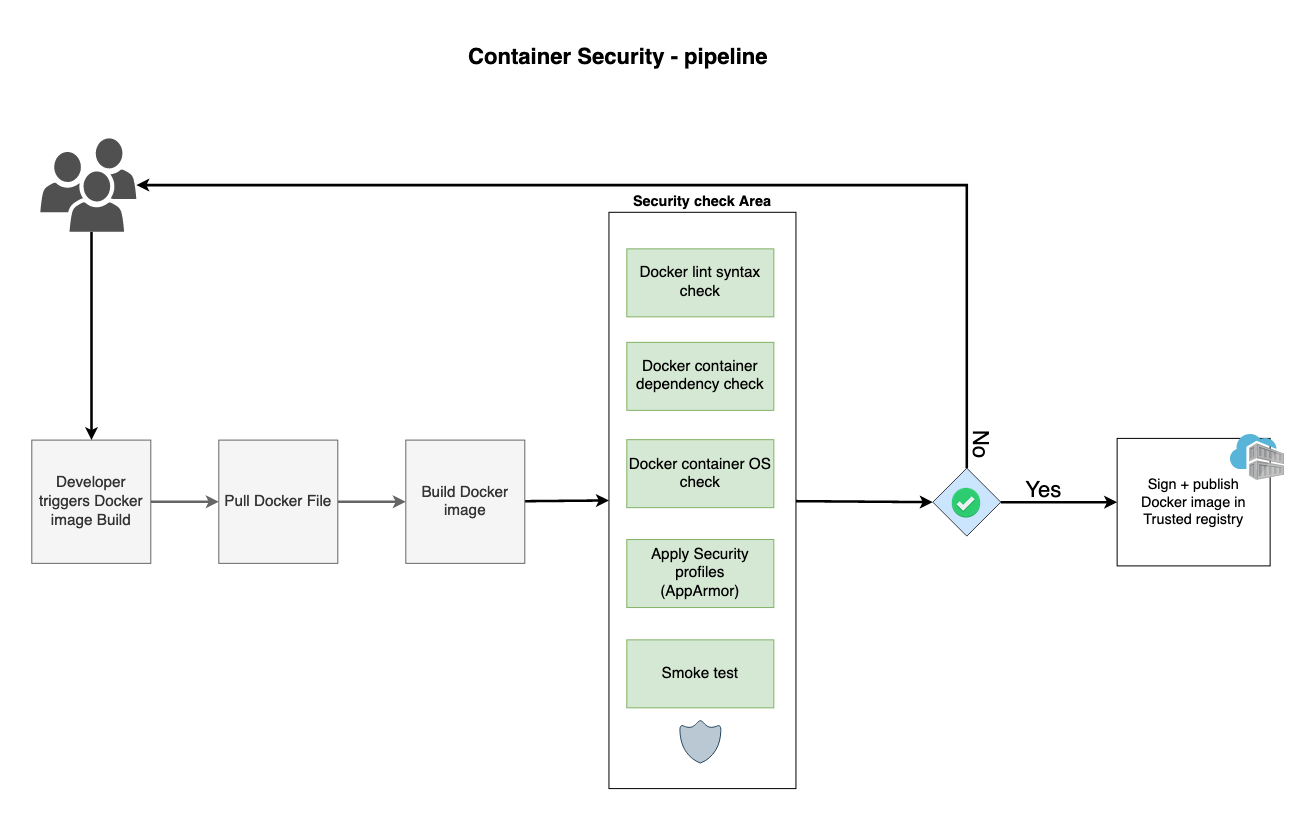
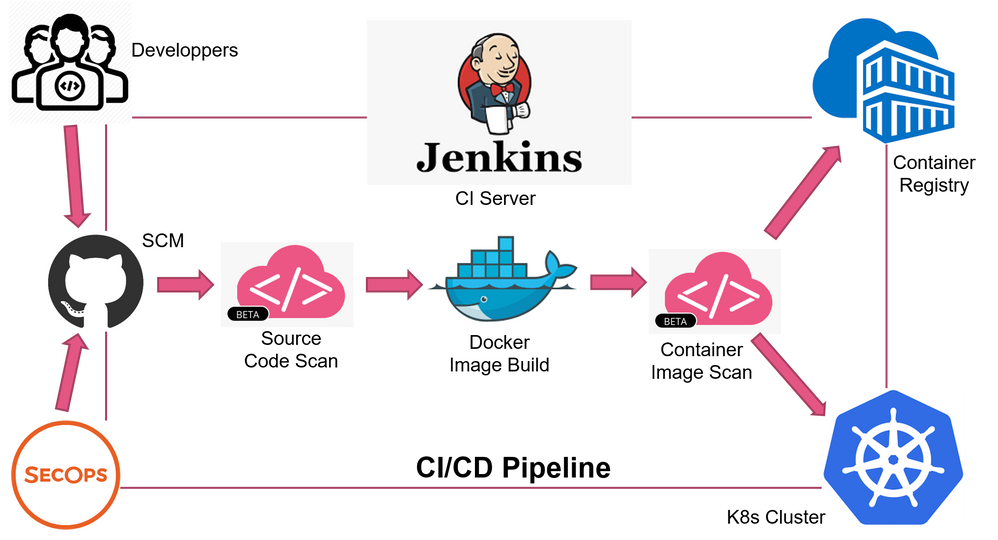
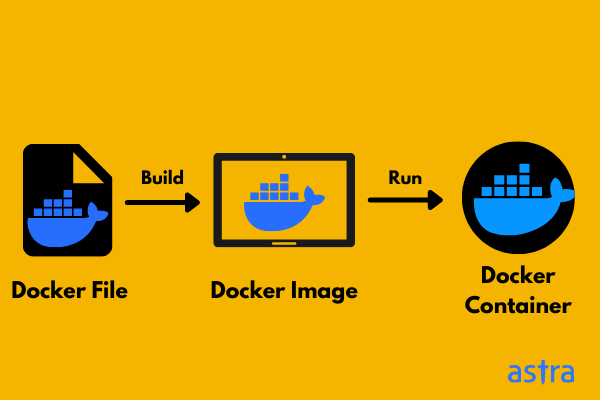
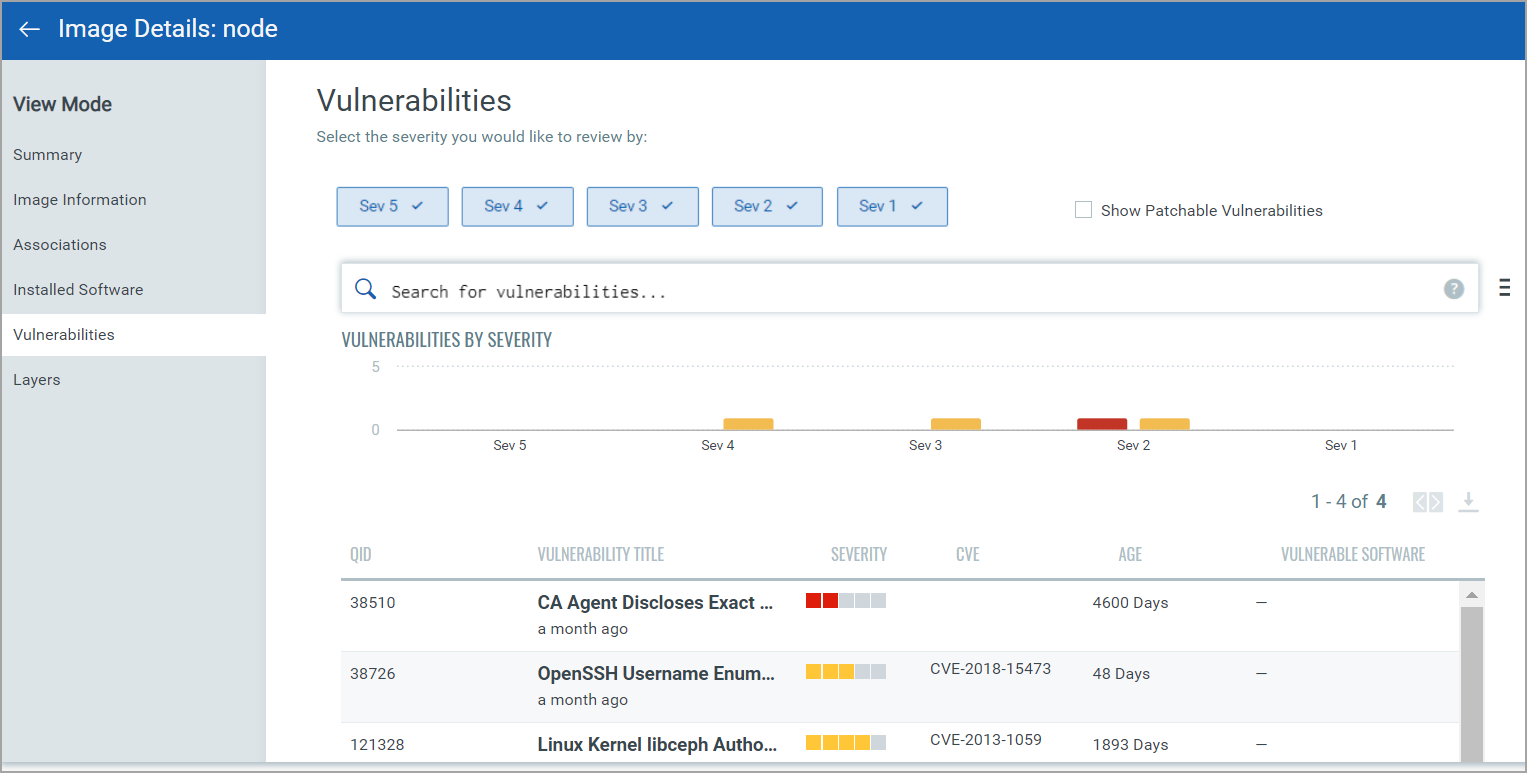
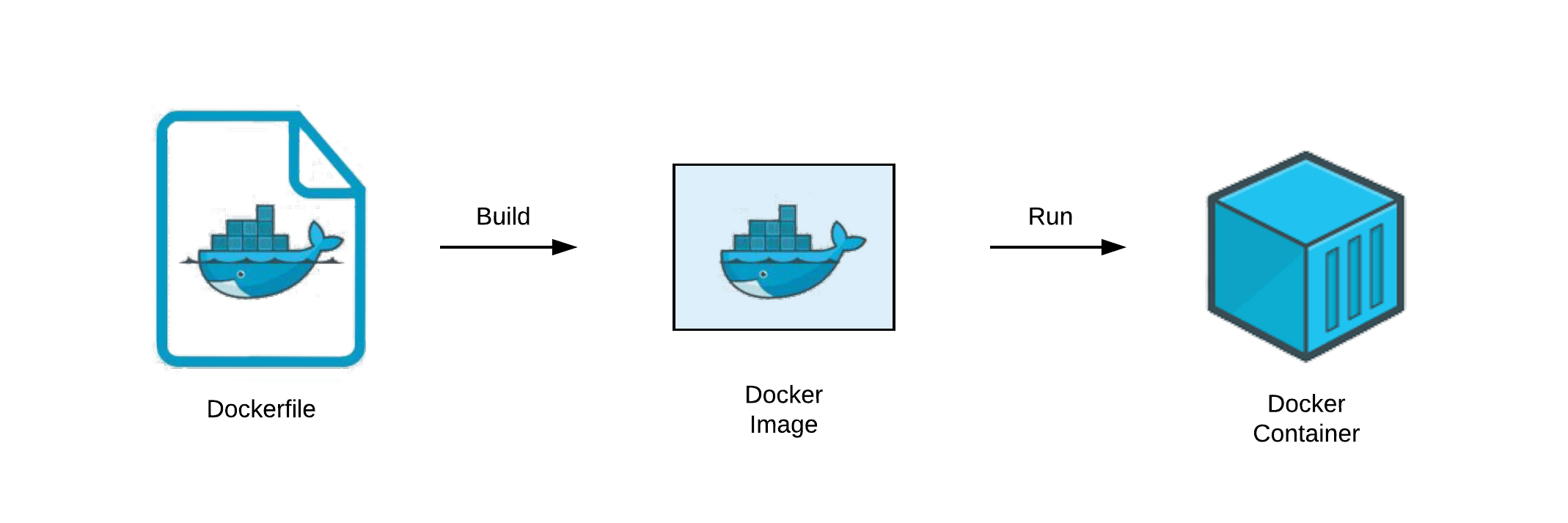
Adding Image Security Scanning to a CI/CD pipeline | by Larbi Youcef Mohamed Reda | alter way | Medium
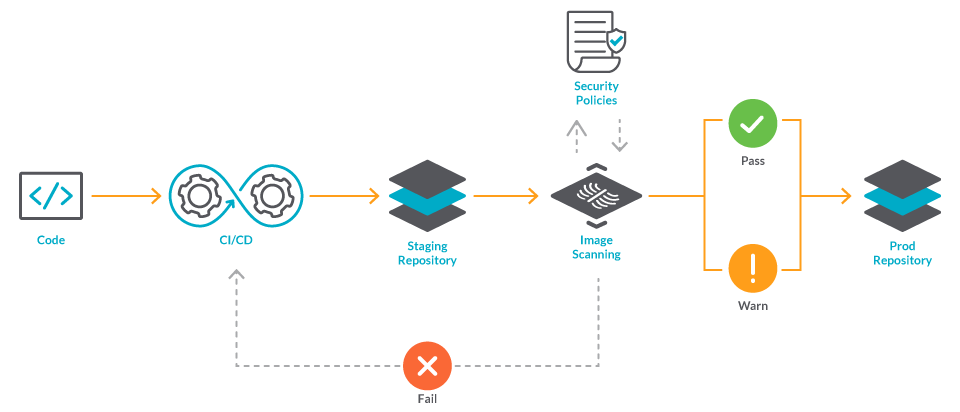
Testing how to use some container vulnerabilities scanners with Azure Pipelines :: my tech ramblings — A blog for writing about my techie ramblings