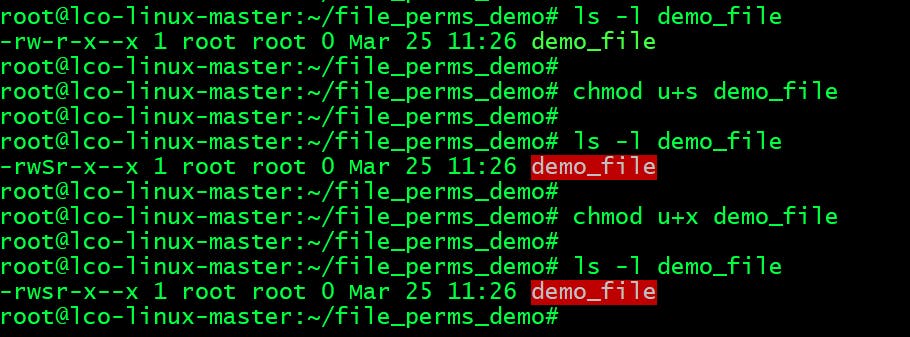
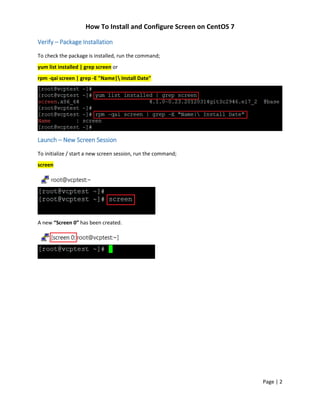
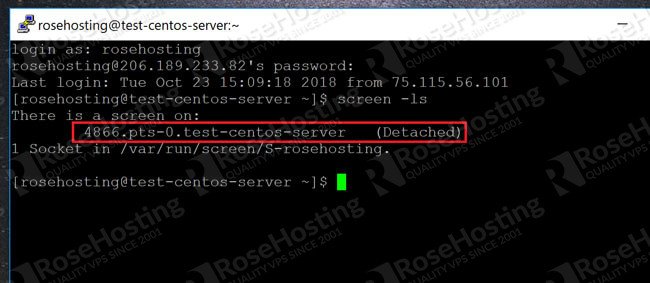
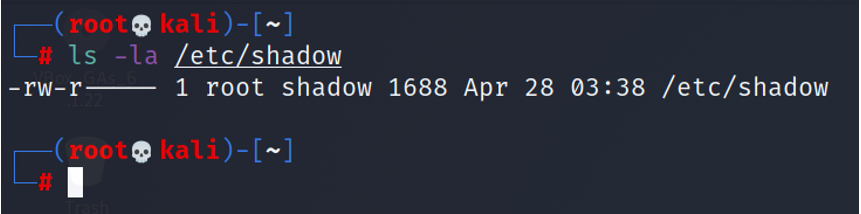
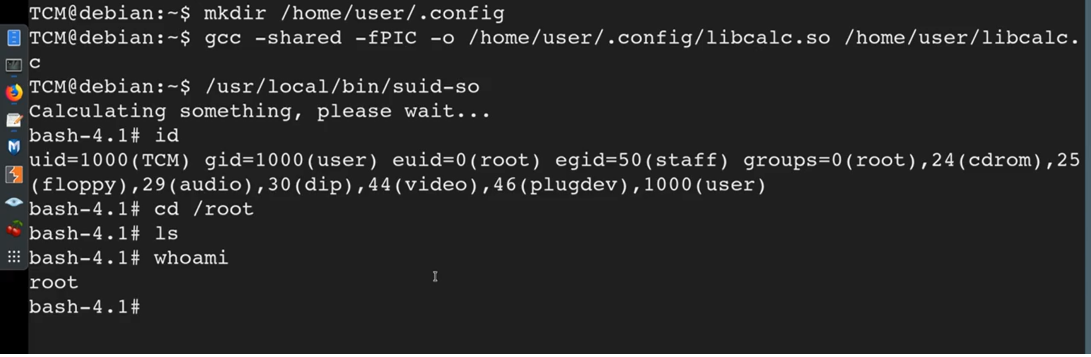
Foundation Topics: Exploiting Local Host Vulnerabilities | Exploiting Local Host and Physical Security Vulnerabilities | Pearson IT Certification
Being a multi-user system - UNIX and Linux have a tremendous amount of security to offer; many being open source, which can be validated and modified. - ppt download