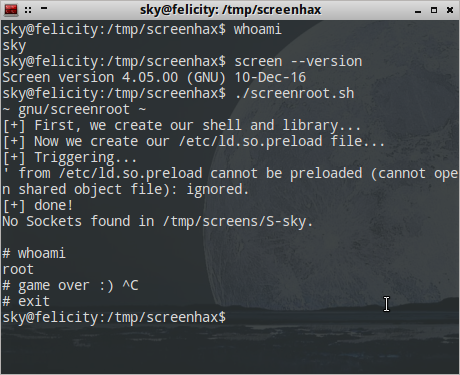
Why is the default file permission 666 in Linux? How is the security effect if the file becomes executable? - Quora
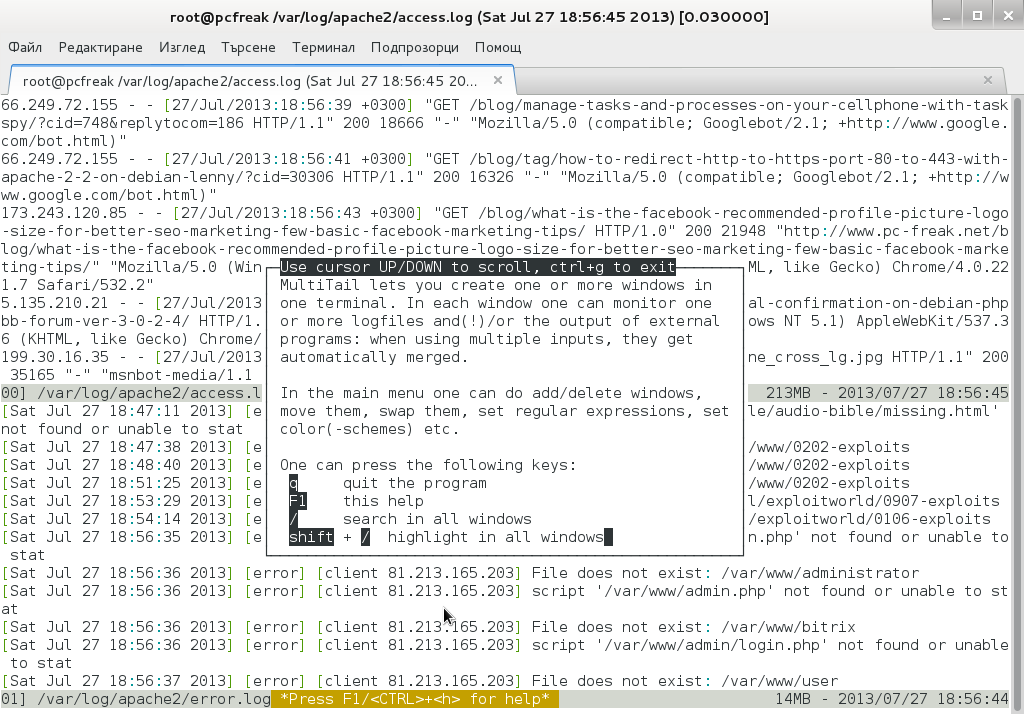
Tracking multiple log files in real time in Linux console / terminal (MultiTail) - ☩ Walking in Light with Christ - Faith, Computing, Diary
GitHub - FOSSClass/AbantOS-Elive: README for AbantOS (Elive/Debian Custom Distribution) Pick a Section, fork, edit, commit, pull, merge